- Home
- Resources
- Work samples
- Samples
- Investigation: Secure networks - ABOVE
Digital Technologies
Years 9 and 10
Above satisfactory
Investigation: Secure networks
Summary of task
Students created and gave a presentation to educate and inform users about data, network communication and security. They identified and described the purpose and components of two different networks, then selected one and created a network topology for it. Students described the security features operating on the network and explained how data (text, image and audio) was kept secure. They described possible upgrades that would improve the overall level of security and described the implications of minimal or no security on the network and its devices.
Students responded to questions on networks in an examination.
Achievement standard
By the end of Year 10, students explain the control and management of networked digital systems and the security implications of the interaction between hardware, software and users. They explain simple data compression, and why content data are separated from presentation. Students plan and manage digital projects using an iterative approach. They define and decompose complex problems in terms of functional and non-functional requirements.
Students design and evaluate user experiences and algorithms. They design and implement modular programs, including an object-oriented program, using algorithms and data structures involving modular functions that reflect the relationships of real-world data and data entities. They take account of privacy and security requirements when selecting and validating data. Students test and predict results and implement digital solutions. They evaluate information systems and their solutions in terms of risk, sustainability and potential for innovation and enterprise. They share and collaborate online, establishing protocols for the use, transmission and maintenance of data and projects.

 1
Annotation 1
1
Annotation 1
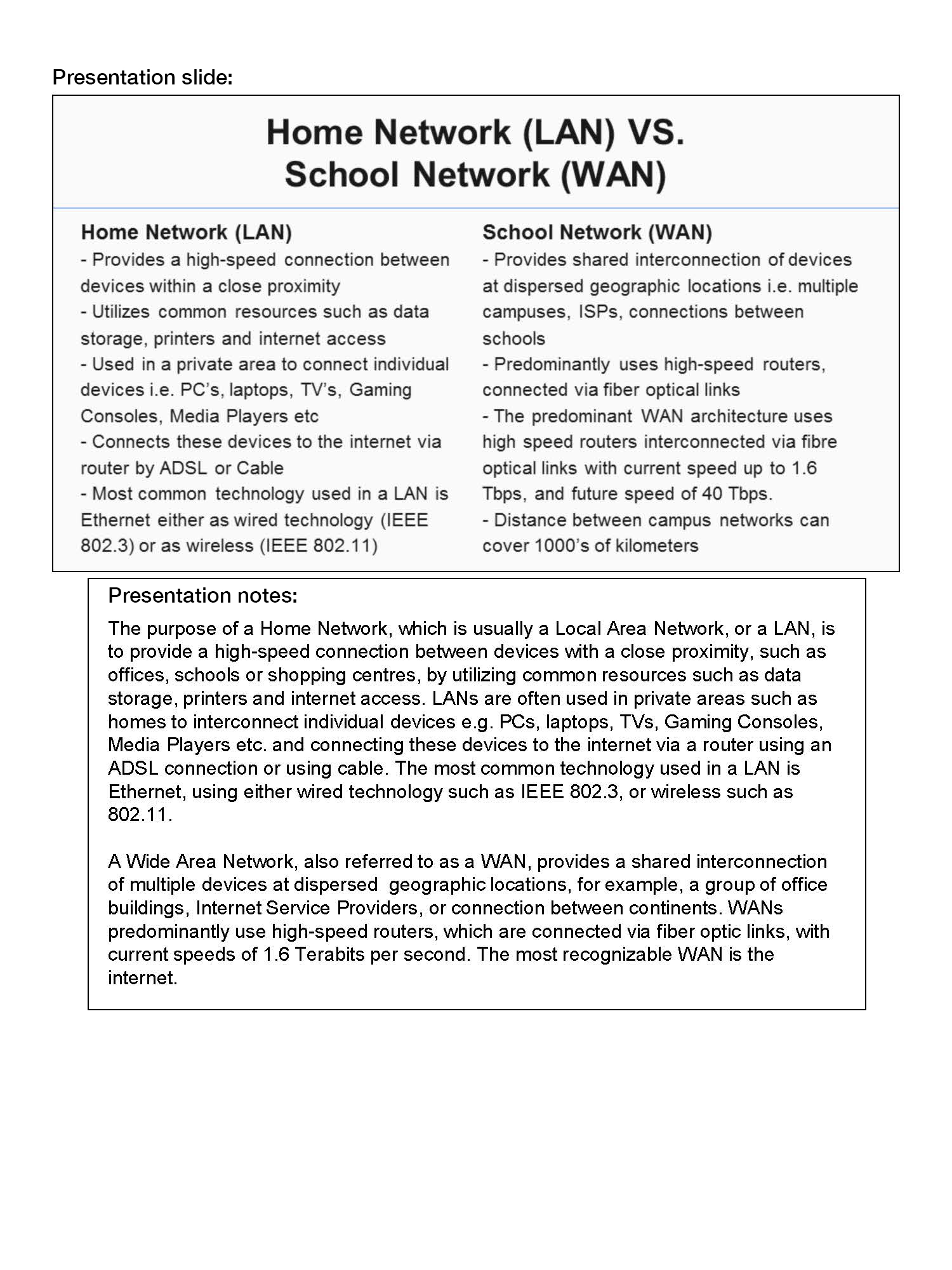
Identifies key differences and similarities between the home local area network (LAN) and the school system wide area network (WAN)
-
Annotations
-
1
Annotation 1
Identifies key differences and similarities between the home local area network (LAN) and the school system wide area network (WAN)
 1
Annotation 1
1
Annotation 1
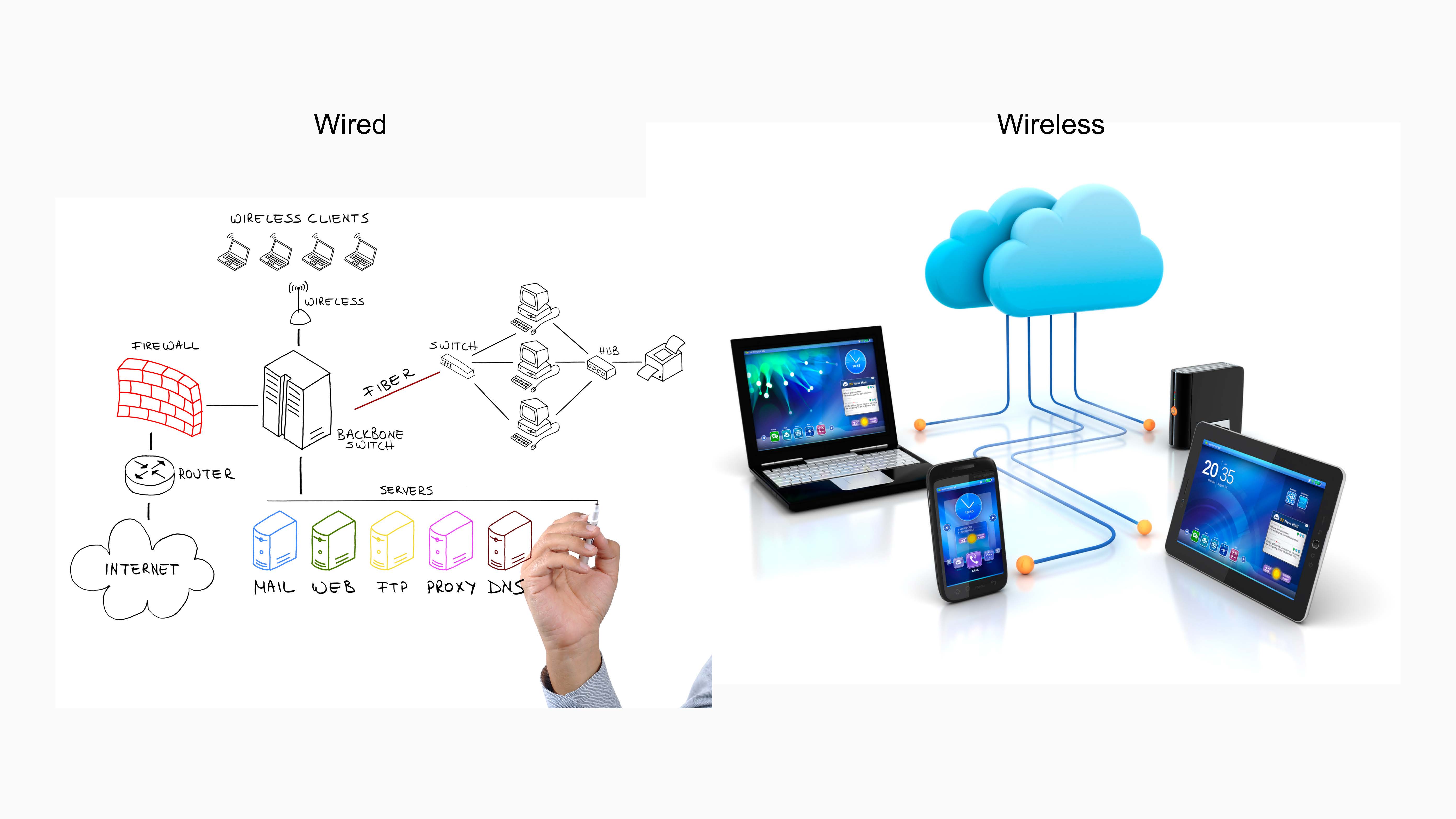
Provides images to illustrate the difference between a LAN and WAN including the interactions between different hardware components
-
Annotations
-
1
Annotation 1
Provides images to illustrate the difference between a LAN and WAN including the interactions between different hardware components
 1
Annotation 1
1
Annotation 1
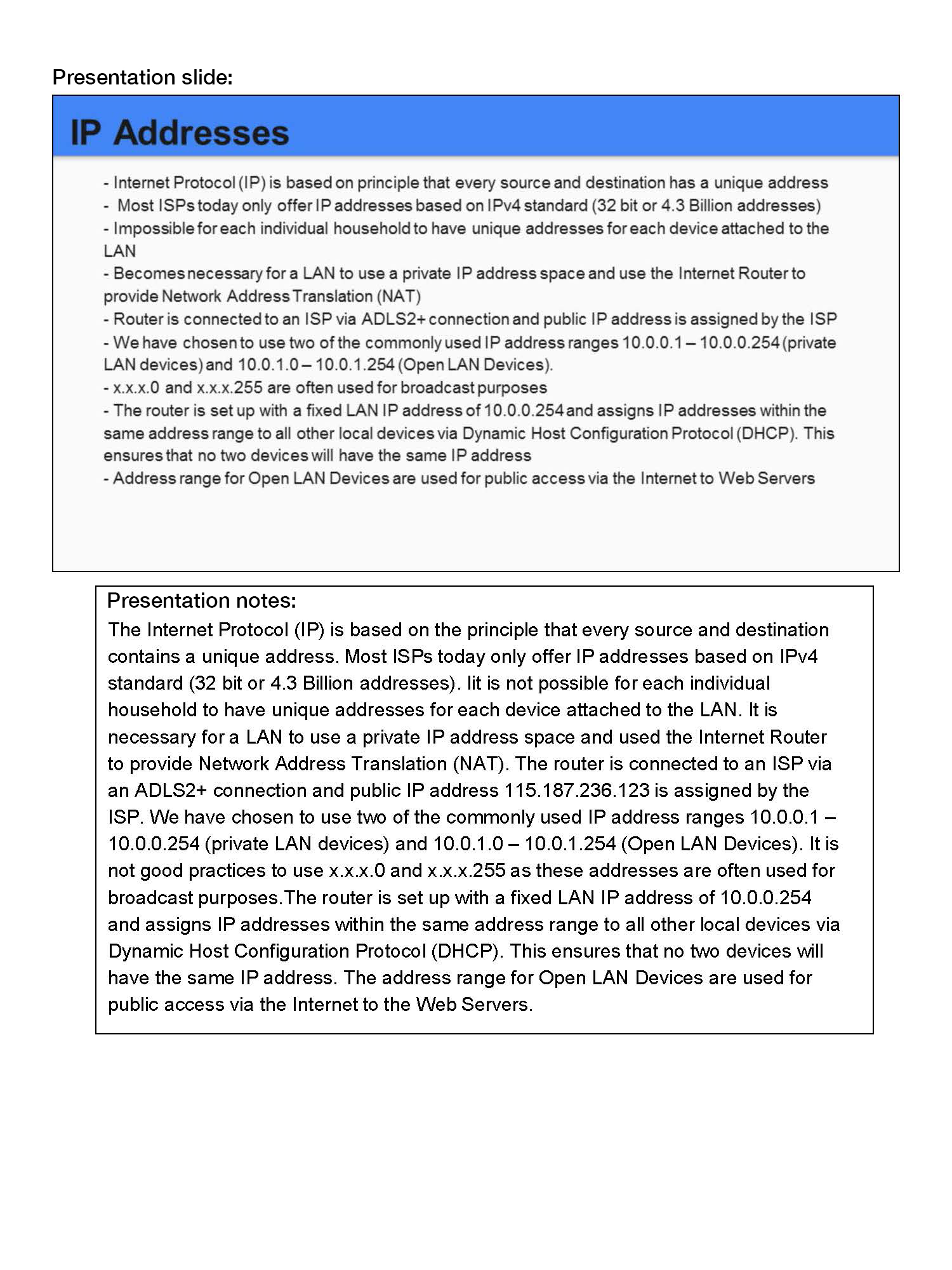
Explains the need for internal management and control hardware, that is, private addressing, and how it allocates addresses
-
Annotations
-
1
Annotation 1
Explains the need for internal management and control hardware, that is, private addressing, and how it allocates addresses
 1
Annotation 1
1
Annotation 1
Identifies a range of security mechanisms and the risks they mitigate
-
Annotations
-
1
Annotation 1
Identifies a range of security mechanisms and the risks they mitigate
 1
Annotation 1
1
Annotation 1
Identifies how data are kept secure on the school network
-
Annotations
-
1
Annotation 1
Identifies how data are kept secure on the school network
 1
Annotation 1
1
Annotation 1
Demonstrates understanding of the concept of the appropriateness of security for a situation, by suggesting how to improve security and identifying the implications of each suggestion
-
Annotations
-
1
Annotation 1
Demonstrates understanding of the concept of the appropriateness of security for a situation, by suggesting how to improve security and identifying the implications of each suggestion
 1
Annotation 1
1
Annotation 1
Explains a range of implications of not taking appropriate security precautions
-
Annotations
-
1
Annotation 1
Explains a range of implications of not taking appropriate security precautions
 1
Annotation 1
1
Annotation 1
Demonstrates knowledge of correct terminology related to data transmission
-
Annotations
-
1
Annotation 1
Demonstrates knowledge of correct terminology related to data transmission
 1
Annotation 1
1
Annotation 1
Demonstrates sound understanding of the interactions between hardware, software and users
-
Annotations
-
1
Annotation 1
Demonstrates sound understanding of the interactions between hardware, software and users
 1
Annotation 1
1
Annotation 1
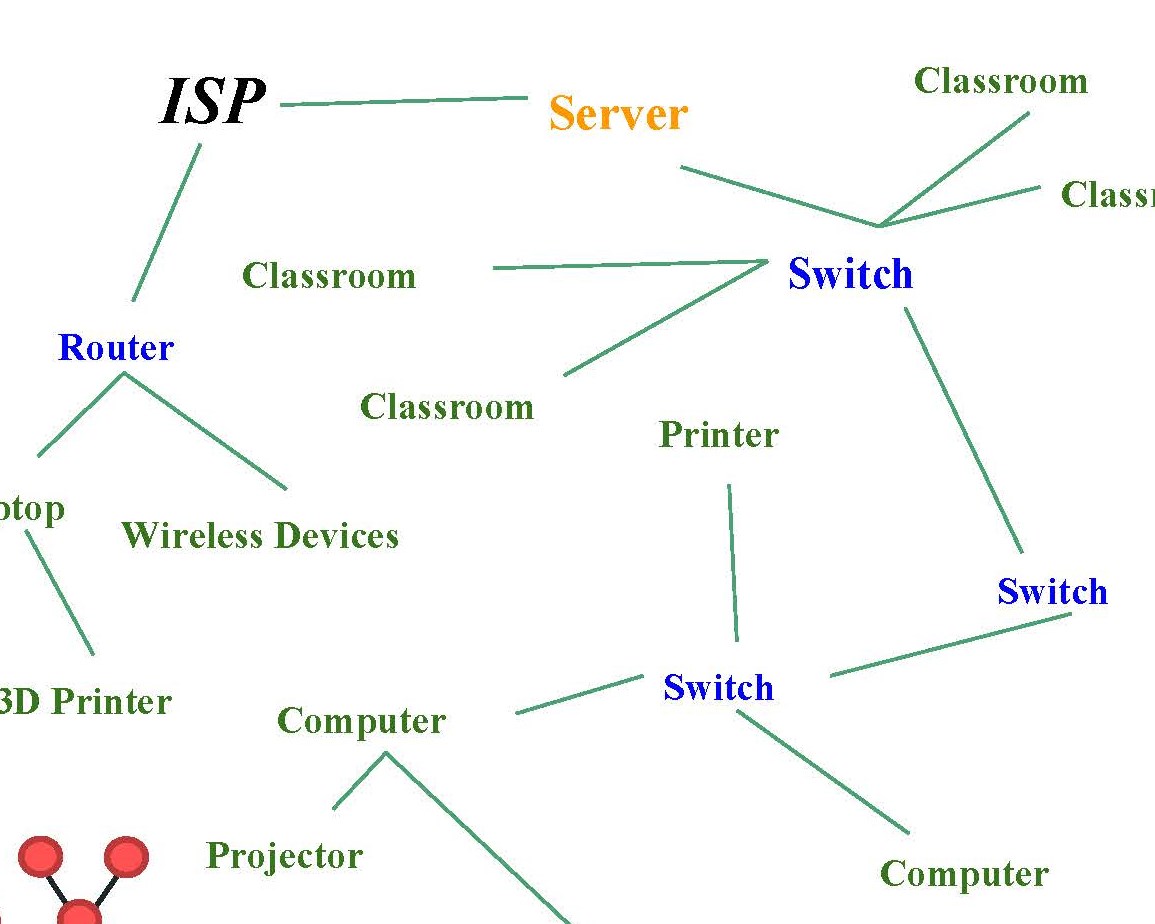
Identifies correctly how hardware is linked together on a network 2 Annotation 2
Summarises succinctly the main features of a star topology and identifies pertinent advantages and disadvantages
-
Annotations
-
1
Annotation 1
Identifies correctly how hardware is linked together on a network -
2
Annotation 2
Summarises succinctly the main features of a star topology and identifies pertinent advantages and disadvantages
 1
Annotation 1
1
Annotation 1
Summarises succinctly the main features of a bus topology and identifies pertinent advantages and disadvantages 2 Annotation 2
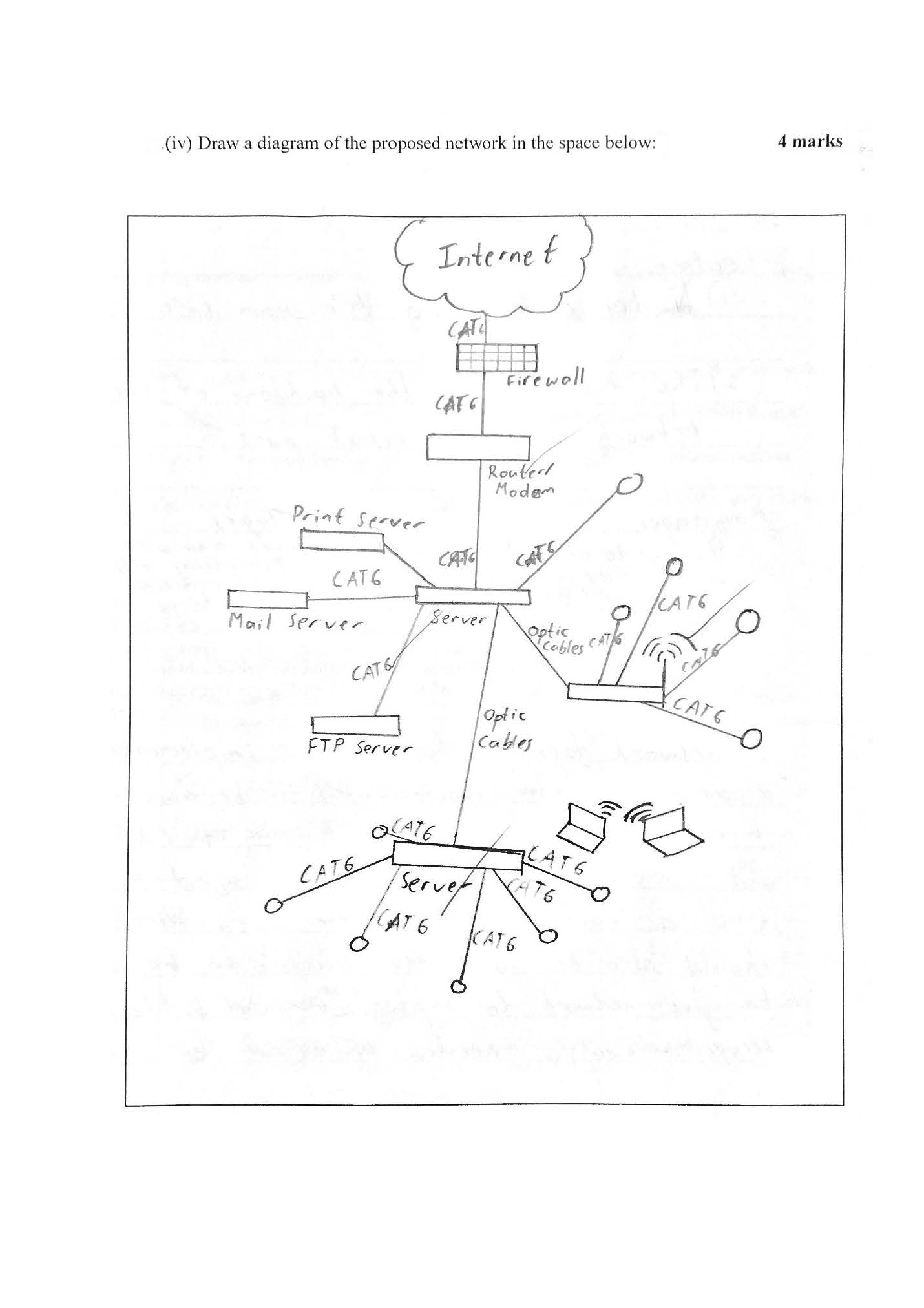
Selects and explains appropriate topology including the mix of technologies required that balance both purpose and performance, and allow for growth
-
Annotations
-
1
Annotation 1
Summarises succinctly the main features of a bus topology and identifies pertinent advantages and disadvantages -
2
Annotation 2
Selects and explains appropriate topology including the mix of technologies required that balance both purpose and performance, and allow for growth
 1
Annotation 1
1
Annotation 1
Draws a diagram of an extended star network including a range of connections and using appropriate conventions
-
Annotations
-
1
Annotation 1
Draws a diagram of an extended star network including a range of connections and using appropriate conventions